Wireshark can decrypt WEP and WPA/WPA2 in pre-shared (or personal) mode. WPA/WPA2 enterprise mode decryption works also since Wireshark 2.0, with some limitations.
You can add decryption keys using Wireshark's 802.11 preferences or by using the wireless toolbar. Up to 64 keys are supported.
Adding Keys: IEEE 802.11 Preferences

Aircrack-ng: When it comes to cracking WEP and WPA based networks, Aircrack-ng is the most. If you are not aware of using GPUs for WPA2 cracking purposes let me tell you, Yes GPUs can be used for WPA2 cracking password hashes and are being used now from a while. There are plenty of tools which uses GPU to boost the WPA2 cracking speed and lets you crack in way much lesser time that your CPU would have the job finished.
If you are looking to learn Wi-Fi password hacking, this newly discovered flaw in WPA/WPA2 protocol will surely help you out. Wifi password hacking has become popular as people are always in search of the free internet. But due to the advancement of technology, hacking wifi, and cracking passwords have become a difficult task to do.
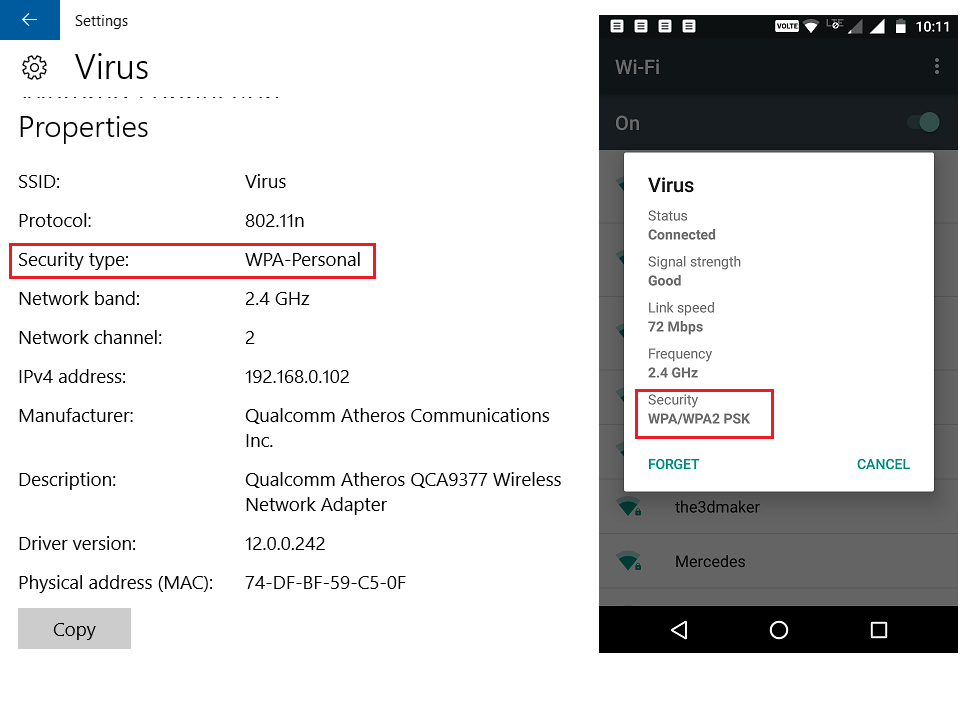
- Using the above methods, you should have known the encryption-type of targeted WiFi network which you want to hack. So, I am gonna show you how to hack WiFi Network for each of WEP, WPA and WPA2 PSK secured WiFi networks.
- For WPA2 decryption to work in wireshark, you will need to capture the 4 authentication packets at the beginning of the connection to the AP. So, disconnect from the SSID, start capturing packets in wireshark, connect to the SSID and you should be able to see the IP (decrypted) traffic.
Go to Edit->Preferences->Protocols->IEEE 802.11. You should see a window that looks like this:
Click on the 'Edit..' button next to 'Decryption Keys' to add keys. You should see a window that looks like this:
When you click the + button to add a new key, there are three key types you can choose from: wep, wpa-pwd, and wpa-psk:
wep The key must be provided as a string of hexadecimal numbers, with or without colons, and will be parsed as a WEP key.
wpa-pwd The password and SSID are used to create a raw pre-shared WPA key.
You can optionally omit the colon and SSID, and Wireshark will try to decrypt packets using the last-seen SSID. This may not work for captures taken in busy environments, since the last-seen SSID may not be correct.
wpa-psk The key is parsed as a raw pre-shared WPA key.
Adding Keys: Wireless Toolbar
If you are using the Windows version of Wireshark and you have an AirPcap adapter you can add decryption keys using the wireless toolbar. If the toolbar isn't visible, you can show it by selecting View->Wireless Toolbar. Click on the Decryption Keys.. button on the toolbar:
This will open the decryption key managment window. As shown in the window you can select between three decryption modes: None, Wireshark, and Driver:
Selecting None disables decryption. Selecting Wireshark uses Wireshark's built-in decryption features. Driver will pass the keys on to the AirPcap adapter so that 802.11 traffic is decrypted before it's passed on to Wireshark. Driver mode only supports WEP keys.
Gotchas
Along with decryption keys there are other preference settings that affect decryption.
Make sure Enable decryption is selected.
You may have to toggle Assume Packets Have FCS and Ignore the Protection bit depending on how your 802.11 driver delivers frames.
The WPA passphrase and SSID preferences let you encode non-printable or otherwise troublesome characters using URI-style percent escapes, e.g. %20 for a space. As a result you have to escape the percent characters themselves using %25.
WPA and WPA2 use keys derived from an EAPOL handshake, which occurs when a machine joins a Wi-Fi network, to encrypt traffic. Unless all four handshake packets are present for the session you're trying to decrypt, Wireshark won't be able to decrypt the traffic. You can use the display filter eapol to locate EAPOL packets in your capture.
In order to capture the handshake for a machine, you will need to force the machine to (re-)join the network while the capture is in progress. One way to do this is to put the machine to sleep (for smartphones and tablets, 'turning off' the machine puts it to sleep) before you start the capture, start the capture, and then wake the machine up. You will need to do this for all machines whose traffic you want to see.
WPA and WPA2 use individual keys for each device. Older versions of Wireshark may only be able to use the most recently calculated session key to decrypt all packets. Therefore, when several devices have attached to the network while the trace was running, the packet overview shows all packets decoded, but in the detailed packet view, only packets of the last device that activated ciphering are properly deciphered. Newer Wireshark versions are able to handle up to 256 associations and should be able to decode any packets all the time. Nevertheless, decoding can still fail if there are too many associations. Filtering out only the relevant packets (e.g. with 'wlan.addr') and saving into a new file should get decryption working in all cases. Wireshark only frees used associations when editing keys or when it's closed. So you may try that when decoding fails for unknown reasons. This also allows you to decode files without any eapol packets in it, as long as Wireshark did see the eapol packets for this communication in another capture after the last start and key edit. If decoding suddenly stops working make sure the needed eapol packetes are still in it.
WPA/WPA2 Enterprise/Rekeys
As long as you can somehow extract the PMK from either the client or the Radius Server and configure the key (as PSK) all supported Wireshark versions will decode the traffic just fine up to the first eapol rekey.
Eapol rekey is often enabled for WPA/WPA2 enterprise and will change the used encryption key similar to the procedure for the initial connect, but it can also be configured and used for pre-shared (personal) mode. Wireshark 2.0 (v1.99.6rc0-454-g1439eb6 or newer) is needed if you want decode packets after a rekey.
Examples
The file SampleCaptures/wpa-Induction.pcap has WPA traffic encrypted using the password 'Induction' and SSID 'Coherer'.
The file SampleCaptures/wpa-eap-tls.pcap.gz has a EAP-TLS handshake and rekeys included. The PMK's you can use as PSK's to decode it are: a5001e18e0b3f792278825bc3abff72d7021d7c157b600470ef730e2490835d4 79258f6ceeecedd3482b92deaabdb675f09bcb4003ef5074f5ddb10a94ebe00a 23a9ee58c7810546ae3e7509fda9f97435778d689e53a54891c56d02f18ca162
CategoryHowTo
If you remember in the previous part, we learned Speeding up WPA2 Cracking Using Pre-generated PMKs. Which certainly uses CPU as the primary part for the calculations of the PMKs. It surely gives us speed for WPA2 cracking as while using PMKs for cracking we are not performing actual calculations in real-time.
This brings us to some drawbacks of using PMKs, as follows:
- SSID Specific. You cannot use PMKs generated for SSID, say 'rootsh3ll' for another SSID like 'Belkin'.
- Case-Sensitive. Cannot be used even a single letter is up/lower case. Ex: Won't work for 'Rootsh3ll' if PMKs are created for 'rootsh3ll'.
- Time used is the same. As processing power of CPU is same in both cases, the time required for creating PMKs are equal even if you crack using Aircrack or creating PMKs(with GenPMK).
- Huge HD Space required. As we are pre-calculating the PMKs and storing them on HD, it requires a lot of space on your HD and that too for a specific SSID. Which is not an option all the time.
- Less helpful in today's scenario. Nowadays routers are being shipped with unique SSID. Ex: Belkin_04A2 for preventing routers from these kind of attacks or atleast delay the cracking duration.
You might be thinking now that If this is so, then why would I even consider PMKs for WPA2 cracking ?
Well, as I said above this is Less helpful, that means in some cases.
Cases like:
- Simple SSIDs. Ex: MTNL, Airtel, Linksys etc
- Before trying any complex task to crack the PSK, if you have PMKs already stored. Give them a shot
- Mobile numbers are still very common passwords.
Still, even if this gives us speed this method is a bit slow. You don't always have a friend ready to give you a pre-generated PMK file for a specific SSID just when you have captured the handshake, right? yeah, it's very rare!
Here is when you need to stop using your CPU and test the processing power of you GPU.
If you are not aware of using GPUs for WPA2 cracking purposes let me tell you, Yes GPUs can be used for WPA2 cracking password hashes and are being used now from a while.
There are plenty of tools which uses GPU to boost the WPA2 cracking speed and lets you crack in way much lesser time that your CPU would have the job finished.
Tools like:
- Pyrit
- BarsWF
- HashCat
- igHashGPU
How ? Simple! Your CPU has 2,4,8 cores, means parallel computing units where GPUs have them in thousands, if not hundreds.
NOTE: My GeForce GT 525M have 296 cores, and it is pretty old Graphics card, Speed: ~6000 PMK/s. NVidia Titan X is the Best single graphics card with cracking speed up to 2,096,000 hashes/sec.
Using GPU for Cracking WPA2 Passwords
Being in the scope of the series we will stick to WPA2 cracking with GPU in this chapter. For learning difference between CPU and GPU cracking you can visit the following post I'd previously written on FromDev.com.
Tools described above are used for cracking various kinds of passwords.
There are 2 tools used for WPA2 cracking using GPU from the above list
- Pyrit
- HashCat
As the post title suggests we will go with HashCat.
What is HashCat ?
Ocl/CUDA/HashCat is now Open Source. Checkout at GitHub: github.com/hashcat
Hashcat is a self-proclaimed command line based world's fastest password cracker.
It is the world's first and only GPGPU based rule engine and available for Linux, OSX, and Windows free-of-cost. It comes in 2 variants
- CPU Based
- GPU Based
There is no difference when passing commands to Hashcat because it automatically uses the best method to crack passwords, either CPU or GPU depending on the Graphics driver you have installed or not.
Hashcat is fast and extremely flexible- to writer made it in such a way that allows distributed cracking. I highly recommend Hashcat over Pyrit for its flexibility.
Why use HashCat at first place ?
As already told above, because of it's flexibility and vast support of algorithms.
But why Hashcat when I just want to WPA2 cracking most of the times ?
If you have used or haven't used Pyrit yet, let me tell you one thing. Pyrit wasthe fastest WPA2 cracker available in its early times but it uses dictionary or wordlist to crack the passwords even if you use PMKs or directly run the cracker you need to have a large amount of dictionaries to test the validity of the hash.
Also Hashcat has been outperforming Pyrit for many years now. and if you are still using Pyrit, Time for switching to Hashcat is now!
For storing hashes you need a lot of disk space. As you can see in the image below, there is a few wordlists that almost take >25 GB on the disk(Extracted), and it take more than 2-3 days to run through them all even with GPU.
You can download some useful wordlists here.
But most of the times there are some pattern(default passwords) we like to test for validity. Patterns like:
- Mobile number
- Date of Birth
- Default password patterns like '56324FHe'
- 10 digit default password by ISP
- and so on
Here is when We have to leave Pyrit with it's dictionaries and get our hands-on with HashCat.
HashCat have a brilliant feature called mask-attack, which allows us to create user-defined patterns to test for password validity and you know what the best thing is ? It requires 0 Bytes on your hard drive.
How ?
Before we go through this we need to understand that in some cases we need Wordlists. Its only when we are 100% certain that it has some kind of pattern we can use this type of attack. So of you know a certain ISP has 10 random numbers and only a few letters, you could do it to save space on your HD.
WPA2 cracking is a tedious task and uses maximum power of the system when we use Hashcat for the purpose and sometimes it needs to take down the load from the system to switch tasks. hashcat stands best here for it's remarkable feature.
- It supports pause/resume while cracking
- Supports sessions and restore
We will see this feature in this tutorial. Keep reading.
Supported Attack types
- Dictionary based attack
- Brute-force/Mask attack
- Hybrid dict + mask
- Hybrid mask + dict
- Permutation attack
- Rule-based attack
- Toggle-case attack
These are too name a few. Hashcat supports way too many algorithms to get your hash cracked.
NOTE: Traditional Brute-force attack is outdated and is replaced by Mask attack in Hashcat. Wee will see later in this post in details about this.
Variants
As told above Hashcat comes in 2 vaiants:
- Hashcat -A CPU based password cracker
- Oclhashcat/CudaHashcat – GPU accelerated tool
Setting up the Lab
Installing Graphics driver
You have basically 2 choices
- Install graphics driver in Kali Linux directly, i.e your Pentesting distro.
- Install graphics driver in Windows or OSX.
I have Kali Sana installed in my Virtual machine and unfortunately no virtual machine supports using graphics card or GPU acceleration inside the virtual OS. So I'll be sticking with Hashcat on windows. You can still do the same task with exact same commands on Kali Linux(or any Linux OS) or OSX with properly installed proprietary drivers.
I haven't written any article on how to install graphics drier in Kali Linux as BlackmoreOps already have a great article on same. so you can follow the links and try installing the same on your version of Kali.
NVidia Users:
AMD Users:
Download HashCat
You can download Hashcat from it's official website: http://hashcat.net/
File is highly compressed using 7z compression. So make sure you have atleast 1 GB before extracting the downloaded file.
You can use 7zip extractor to decompress the .7z file. Download it here: http://www.7-zip.org/download.html

P.S: It is free of use and better than WinRAR.
Cleanup your cap file using wpaclean
Next step will be converting the .cap file to a format cudaHashcat or oclHashcat or Hashcat on Kali Linux will understand.
Here's how to do it:
To convert your .cap files manually in Kali Linux, use the following command
Please note that the wpaclean options are the wrong way round. <out.cap> <in.cap> instead of <in.cap> <out.cap> which may cause some confusion. Workforce 13 in 1 screwdriver 1/2.
Convert .cap file to .hccapx file
Now assuming that you have installed appropriate graphics driver for the selected OS, moving on to the nest step. We need to convert the previously captured handshake i.e .cap file to a format that hashcat could understand and it is .hccapx file format.
Nothing difficult or time taking. Command to convert .cap to .hccapx goes like this
- aircrack-ng -j
Here output.hccapx is the output filename with .hccapx file format and input.cap is the handshake originally captured.
Log in to Kali Linux, open Terminal and type:
Note: rootsh3ll-01.cap is located on Desktop. Check location of your .cap file.
Now we have .hccapx file, installed graphics driver and downloaded hashcat. Let's begin the cracking.
Cracking WPA2 Passwords using Hashcat
We will cover the following topics:
- WPA2 Cracking with Dictionary attack using Hashcat.
- WPA2 Cracking with Mask attack using Hashcat.
- WPA2 Cracking with Hybrid attack using Hashcat.
- WPA2 Cracking Pause/resume in Hashcat (One of the best features)
- WPA2 Cracking save sessions and restore.
WPA2 dictionary attack using Hashcat
Open cmd and direct it to Hashcat directory, copy .hccapx file and wordlists and simply type in cmd
Here I have NVidia's graphics card so I use CudaHashcat command followed by 64, as I am using Windows 10 64-bit version. yours will depend on graphics card you are using and Windows version(32/64).
cudaHashcat64.exe – The program, In the same folder theres a cudaHashcat32.exe for 32 bit OS and cudaHashcat32.bin / cudaHashcat64.bin for Linux. oclHashcat*.exe for AMD graphics card.
-m 2500 = The specific hashtype. 2500 means WPA/WPA2.
In case you forget the WPA2 code for Hashcat.
Windows CMD: cudaHashcat64.exe –help | find 'WPA'
Linux Terminal:cudaHashcat64.bin –help | grep 'WPA'
It will show you the line containing 'WPA' and corresponding code.
Handshake-01.hccap = The converted *.cap file.
wordlist.txt wordlist2.txt= The wordlists, you can add as many wordlists as you want. To simplify it a bit, every wordlist you make should be saved in the CudaHashcat folder.
After executing the command you should see a similar output:
Wait for Hashcat to finish the task. You can pass multiple wordlists at once so that Hashcat will keep on testing next wordlist until the password is matched.
WPA2 Mask attack using Hashcat
As told earlier, Mask attack is a replacement of the traditional Brute-force attack in Hashcat for better and faster results.
Aircrack-ng: When it comes to cracking WEP and WPA based networks, Aircrack-ng is the most. If you are not aware of using GPUs for WPA2 cracking purposes let me tell you, Yes GPUs can be used for WPA2 cracking password hashes and are being used now from a while. There are plenty of tools which uses GPU to boost the WPA2 cracking speed and lets you crack in way much lesser time that your CPU would have the job finished.
If you are looking to learn Wi-Fi password hacking, this newly discovered flaw in WPA/WPA2 protocol will surely help you out. Wifi password hacking has become popular as people are always in search of the free internet. But due to the advancement of technology, hacking wifi, and cracking passwords have become a difficult task to do.
- Using the above methods, you should have known the encryption-type of targeted WiFi network which you want to hack. So, I am gonna show you how to hack WiFi Network for each of WEP, WPA and WPA2 PSK secured WiFi networks.
- For WPA2 decryption to work in wireshark, you will need to capture the 4 authentication packets at the beginning of the connection to the AP. So, disconnect from the SSID, start capturing packets in wireshark, connect to the SSID and you should be able to see the IP (decrypted) traffic.
Go to Edit->Preferences->Protocols->IEEE 802.11. You should see a window that looks like this:
Click on the 'Edit..' button next to 'Decryption Keys' to add keys. You should see a window that looks like this:
When you click the + button to add a new key, there are three key types you can choose from: wep, wpa-pwd, and wpa-psk:
wep The key must be provided as a string of hexadecimal numbers, with or without colons, and will be parsed as a WEP key.
wpa-pwd The password and SSID are used to create a raw pre-shared WPA key.
You can optionally omit the colon and SSID, and Wireshark will try to decrypt packets using the last-seen SSID. This may not work for captures taken in busy environments, since the last-seen SSID may not be correct.
wpa-psk The key is parsed as a raw pre-shared WPA key.
Adding Keys: Wireless Toolbar
If you are using the Windows version of Wireshark and you have an AirPcap adapter you can add decryption keys using the wireless toolbar. If the toolbar isn't visible, you can show it by selecting View->Wireless Toolbar. Click on the Decryption Keys.. button on the toolbar:
This will open the decryption key managment window. As shown in the window you can select between three decryption modes: None, Wireshark, and Driver:
Selecting None disables decryption. Selecting Wireshark uses Wireshark's built-in decryption features. Driver will pass the keys on to the AirPcap adapter so that 802.11 traffic is decrypted before it's passed on to Wireshark. Driver mode only supports WEP keys.
Gotchas
Along with decryption keys there are other preference settings that affect decryption.
Make sure Enable decryption is selected.
You may have to toggle Assume Packets Have FCS and Ignore the Protection bit depending on how your 802.11 driver delivers frames.
The WPA passphrase and SSID preferences let you encode non-printable or otherwise troublesome characters using URI-style percent escapes, e.g. %20 for a space. As a result you have to escape the percent characters themselves using %25.
WPA and WPA2 use keys derived from an EAPOL handshake, which occurs when a machine joins a Wi-Fi network, to encrypt traffic. Unless all four handshake packets are present for the session you're trying to decrypt, Wireshark won't be able to decrypt the traffic. You can use the display filter eapol to locate EAPOL packets in your capture.
In order to capture the handshake for a machine, you will need to force the machine to (re-)join the network while the capture is in progress. One way to do this is to put the machine to sleep (for smartphones and tablets, 'turning off' the machine puts it to sleep) before you start the capture, start the capture, and then wake the machine up. You will need to do this for all machines whose traffic you want to see.
WPA and WPA2 use individual keys for each device. Older versions of Wireshark may only be able to use the most recently calculated session key to decrypt all packets. Therefore, when several devices have attached to the network while the trace was running, the packet overview shows all packets decoded, but in the detailed packet view, only packets of the last device that activated ciphering are properly deciphered. Newer Wireshark versions are able to handle up to 256 associations and should be able to decode any packets all the time. Nevertheless, decoding can still fail if there are too many associations. Filtering out only the relevant packets (e.g. with 'wlan.addr') and saving into a new file should get decryption working in all cases. Wireshark only frees used associations when editing keys or when it's closed. So you may try that when decoding fails for unknown reasons. This also allows you to decode files without any eapol packets in it, as long as Wireshark did see the eapol packets for this communication in another capture after the last start and key edit. If decoding suddenly stops working make sure the needed eapol packetes are still in it.
WPA/WPA2 Enterprise/Rekeys
As long as you can somehow extract the PMK from either the client or the Radius Server and configure the key (as PSK) all supported Wireshark versions will decode the traffic just fine up to the first eapol rekey.
Eapol rekey is often enabled for WPA/WPA2 enterprise and will change the used encryption key similar to the procedure for the initial connect, but it can also be configured and used for pre-shared (personal) mode. Wireshark 2.0 (v1.99.6rc0-454-g1439eb6 or newer) is needed if you want decode packets after a rekey.
Examples
The file SampleCaptures/wpa-Induction.pcap has WPA traffic encrypted using the password 'Induction' and SSID 'Coherer'.
The file SampleCaptures/wpa-eap-tls.pcap.gz has a EAP-TLS handshake and rekeys included. The PMK's you can use as PSK's to decode it are: a5001e18e0b3f792278825bc3abff72d7021d7c157b600470ef730e2490835d4 79258f6ceeecedd3482b92deaabdb675f09bcb4003ef5074f5ddb10a94ebe00a 23a9ee58c7810546ae3e7509fda9f97435778d689e53a54891c56d02f18ca162
CategoryHowTo
If you remember in the previous part, we learned Speeding up WPA2 Cracking Using Pre-generated PMKs. Which certainly uses CPU as the primary part for the calculations of the PMKs. It surely gives us speed for WPA2 cracking as while using PMKs for cracking we are not performing actual calculations in real-time.
This brings us to some drawbacks of using PMKs, as follows:
- SSID Specific. You cannot use PMKs generated for SSID, say 'rootsh3ll' for another SSID like 'Belkin'.
- Case-Sensitive. Cannot be used even a single letter is up/lower case. Ex: Won't work for 'Rootsh3ll' if PMKs are created for 'rootsh3ll'.
- Time used is the same. As processing power of CPU is same in both cases, the time required for creating PMKs are equal even if you crack using Aircrack or creating PMKs(with GenPMK).
- Huge HD Space required. As we are pre-calculating the PMKs and storing them on HD, it requires a lot of space on your HD and that too for a specific SSID. Which is not an option all the time.
- Less helpful in today's scenario. Nowadays routers are being shipped with unique SSID. Ex: Belkin_04A2 for preventing routers from these kind of attacks or atleast delay the cracking duration.
You might be thinking now that If this is so, then why would I even consider PMKs for WPA2 cracking ?
Well, as I said above this is Less helpful, that means in some cases.
Cases like:
- Simple SSIDs. Ex: MTNL, Airtel, Linksys etc
- Before trying any complex task to crack the PSK, if you have PMKs already stored. Give them a shot
- Mobile numbers are still very common passwords.
Still, even if this gives us speed this method is a bit slow. You don't always have a friend ready to give you a pre-generated PMK file for a specific SSID just when you have captured the handshake, right? yeah, it's very rare!
Here is when you need to stop using your CPU and test the processing power of you GPU.
If you are not aware of using GPUs for WPA2 cracking purposes let me tell you, Yes GPUs can be used for WPA2 cracking password hashes and are being used now from a while.
There are plenty of tools which uses GPU to boost the WPA2 cracking speed and lets you crack in way much lesser time that your CPU would have the job finished.
Tools like:
- Pyrit
- BarsWF
- HashCat
- igHashGPU
How ? Simple! Your CPU has 2,4,8 cores, means parallel computing units where GPUs have them in thousands, if not hundreds.
NOTE: My GeForce GT 525M have 296 cores, and it is pretty old Graphics card, Speed: ~6000 PMK/s. NVidia Titan X is the Best single graphics card with cracking speed up to 2,096,000 hashes/sec.
Using GPU for Cracking WPA2 Passwords
Being in the scope of the series we will stick to WPA2 cracking with GPU in this chapter. For learning difference between CPU and GPU cracking you can visit the following post I'd previously written on FromDev.com.
Tools described above are used for cracking various kinds of passwords.
There are 2 tools used for WPA2 cracking using GPU from the above list
- Pyrit
- HashCat
As the post title suggests we will go with HashCat.
What is HashCat ?
Ocl/CUDA/HashCat is now Open Source. Checkout at GitHub: github.com/hashcat
Hashcat is a self-proclaimed command line based world's fastest password cracker.
It is the world's first and only GPGPU based rule engine and available for Linux, OSX, and Windows free-of-cost. It comes in 2 variants
- CPU Based
- GPU Based
There is no difference when passing commands to Hashcat because it automatically uses the best method to crack passwords, either CPU or GPU depending on the Graphics driver you have installed or not.
Hashcat is fast and extremely flexible- to writer made it in such a way that allows distributed cracking. I highly recommend Hashcat over Pyrit for its flexibility.
Why use HashCat at first place ?
As already told above, because of it's flexibility and vast support of algorithms.
But why Hashcat when I just want to WPA2 cracking most of the times ?
If you have used or haven't used Pyrit yet, let me tell you one thing. Pyrit wasthe fastest WPA2 cracker available in its early times but it uses dictionary or wordlist to crack the passwords even if you use PMKs or directly run the cracker you need to have a large amount of dictionaries to test the validity of the hash.
Also Hashcat has been outperforming Pyrit for many years now. and if you are still using Pyrit, Time for switching to Hashcat is now!
For storing hashes you need a lot of disk space. As you can see in the image below, there is a few wordlists that almost take >25 GB on the disk(Extracted), and it take more than 2-3 days to run through them all even with GPU.
You can download some useful wordlists here.
But most of the times there are some pattern(default passwords) we like to test for validity. Patterns like:
- Mobile number
- Date of Birth
- Default password patterns like '56324FHe'
- 10 digit default password by ISP
- and so on
Here is when We have to leave Pyrit with it's dictionaries and get our hands-on with HashCat.
HashCat have a brilliant feature called mask-attack, which allows us to create user-defined patterns to test for password validity and you know what the best thing is ? It requires 0 Bytes on your hard drive.
How ?
Before we go through this we need to understand that in some cases we need Wordlists. Its only when we are 100% certain that it has some kind of pattern we can use this type of attack. So of you know a certain ISP has 10 random numbers and only a few letters, you could do it to save space on your HD.
WPA2 cracking is a tedious task and uses maximum power of the system when we use Hashcat for the purpose and sometimes it needs to take down the load from the system to switch tasks. hashcat stands best here for it's remarkable feature.
- It supports pause/resume while cracking
- Supports sessions and restore
We will see this feature in this tutorial. Keep reading.
Supported Attack types
- Dictionary based attack
- Brute-force/Mask attack
- Hybrid dict + mask
- Hybrid mask + dict
- Permutation attack
- Rule-based attack
- Toggle-case attack
These are too name a few. Hashcat supports way too many algorithms to get your hash cracked.
NOTE: Traditional Brute-force attack is outdated and is replaced by Mask attack in Hashcat. Wee will see later in this post in details about this.
Variants
As told above Hashcat comes in 2 vaiants:
- Hashcat -A CPU based password cracker
- Oclhashcat/CudaHashcat – GPU accelerated tool
Setting up the Lab
Installing Graphics driver
You have basically 2 choices
- Install graphics driver in Kali Linux directly, i.e your Pentesting distro.
- Install graphics driver in Windows or OSX.
I have Kali Sana installed in my Virtual machine and unfortunately no virtual machine supports using graphics card or GPU acceleration inside the virtual OS. So I'll be sticking with Hashcat on windows. You can still do the same task with exact same commands on Kali Linux(or any Linux OS) or OSX with properly installed proprietary drivers.
I haven't written any article on how to install graphics drier in Kali Linux as BlackmoreOps already have a great article on same. so you can follow the links and try installing the same on your version of Kali.
NVidia Users:
AMD Users:
Download HashCat
You can download Hashcat from it's official website: http://hashcat.net/
File is highly compressed using 7z compression. So make sure you have atleast 1 GB before extracting the downloaded file.
You can use 7zip extractor to decompress the .7z file. Download it here: http://www.7-zip.org/download.html
P.S: It is free of use and better than WinRAR.
Cleanup your cap file using wpaclean
Next step will be converting the .cap file to a format cudaHashcat or oclHashcat or Hashcat on Kali Linux will understand.
Here's how to do it:
To convert your .cap files manually in Kali Linux, use the following command
Please note that the wpaclean options are the wrong way round. <out.cap> <in.cap> instead of <in.cap> <out.cap> which may cause some confusion. Workforce 13 in 1 screwdriver 1/2.
Convert .cap file to .hccapx file
Now assuming that you have installed appropriate graphics driver for the selected OS, moving on to the nest step. We need to convert the previously captured handshake i.e .cap file to a format that hashcat could understand and it is .hccapx file format.
Nothing difficult or time taking. Command to convert .cap to .hccapx goes like this
- aircrack-ng -j
Here output.hccapx is the output filename with .hccapx file format and input.cap is the handshake originally captured.
Log in to Kali Linux, open Terminal and type:
Note: rootsh3ll-01.cap is located on Desktop. Check location of your .cap file.
Now we have .hccapx file, installed graphics driver and downloaded hashcat. Let's begin the cracking.
Cracking WPA2 Passwords using Hashcat
We will cover the following topics:
- WPA2 Cracking with Dictionary attack using Hashcat.
- WPA2 Cracking with Mask attack using Hashcat.
- WPA2 Cracking with Hybrid attack using Hashcat.
- WPA2 Cracking Pause/resume in Hashcat (One of the best features)
- WPA2 Cracking save sessions and restore.
WPA2 dictionary attack using Hashcat
Open cmd and direct it to Hashcat directory, copy .hccapx file and wordlists and simply type in cmd
Here I have NVidia's graphics card so I use CudaHashcat command followed by 64, as I am using Windows 10 64-bit version. yours will depend on graphics card you are using and Windows version(32/64).
cudaHashcat64.exe – The program, In the same folder theres a cudaHashcat32.exe for 32 bit OS and cudaHashcat32.bin / cudaHashcat64.bin for Linux. oclHashcat*.exe for AMD graphics card.
-m 2500 = The specific hashtype. 2500 means WPA/WPA2.
In case you forget the WPA2 code for Hashcat.
Windows CMD: cudaHashcat64.exe –help | find 'WPA'
Linux Terminal:cudaHashcat64.bin –help | grep 'WPA'
It will show you the line containing 'WPA' and corresponding code.
Handshake-01.hccap = The converted *.cap file.
wordlist.txt wordlist2.txt= The wordlists, you can add as many wordlists as you want. To simplify it a bit, every wordlist you make should be saved in the CudaHashcat folder.
After executing the command you should see a similar output:
Wait for Hashcat to finish the task. You can pass multiple wordlists at once so that Hashcat will keep on testing next wordlist until the password is matched.
WPA2 Mask attack using Hashcat
As told earlier, Mask attack is a replacement of the traditional Brute-force attack in Hashcat for better and faster results.
let's have a look at what Mask attack really is.
In Terminal/cmd type:
- cudaHashcat64.exe -m 2500 -a 3 ?d?l?u?d?d?d?u?d?s?a
-a 3 is the Attack mode, custom-character set (Mask attack)
?d?l?u?d?d?d?u?d?s?a is the character-set we passed to Hashcat. Let's understand it in a bit of detail that
- What is a character set in Hashcat ?
- Why it is useful ?
What is a character set in Hashcat ?
?d ?l ?u ?d ?d ?d ?u ?d ?s ?a = 10 letters and digits long WPA key. Can be 8-63 char long.
The above text string is called the 'Mask'. Every pair we used in the above examples will translate into the corresponding character that can be an Alphabet/Digit/Special character.
For remembering, just see the character used to describe the charset
?d: For digits
?s: For Special characters
?u: For Uppercase alphabets
?l: For Lowercase alphabets
?a: all of the above.
Simple! isn't it ?
Here is the actual character set which tells exactly about what characters are included in the list:
Here are a few examples of how the PSK would look like when passed a specific Mask.
PSK = ?d?l?u?d?d?d?u?d?s?a
0aC575G2/@
9zG432H0*K
8sA111W1$4
3wD001Q5+z
So now you should have a good understanding of the mask attack, right ?
Let's dig a bit deeper now.
Mixing Mask attack with Custom characters.
Let's say, we somehow came to know a part of the password. So, it would be better if we put that part in the attack and randomize the remaining part in Hashcat, isn't it ?
Sure! it is very simple. Just put the desired characters in the place and rest with the Mask.
He ?d ?l 123 ?d ?d ?u ?d C is the custom Mask attack we have used. Here assuming that I know the first 2 characters of the original password then setting the 2nd and third character as digit and lowercase letter followed by '123' and then '?d ?d ?u ?d' and finally ending with 'C' as I knew already.
What we have actually done is that we have simply placed the characters in the exact position we knew and Masked the unknown characters, hence leaving it on to Hashcat to test further.
Here is one more example for the same:
Let's say password is 'Hi123World' and I just know the 'Hi123' part of the password, and remaining are lowercase letters. Assuming length of password to be 10.
So I would simply use the command below
Where ?u will be replaced by uppercase letters, one by one till the password is matched or the possibilities are exhausted.
Moving on even further with Mask attack i.r the Hybrid attack.
In hybrid attack what we actually do is we don't pass any specific string to hashcat manually, but automate it by passing a wordlist to Hashcat.
Hashcat picks up words one by one and test them to the every password possible by the Mask defined.
Example:
- cudaHashcat64.exe -m 2500 handshake.hccapx -a 1 password.txt ?d?l?d?l
-a 1 : The hybrid attack
password.txt : wordlist
?d?l?d?l = Mask (4 letters and numbers)
The wordlist contains 4 words.
Now it will use the words and combine it with the defined Mask and output should be this:
carlos2e1c
bigfoot0h1d
guest5p4a
onion1h1h
It is cool that you can even reverse the order of the mask, means you can simply put the mask before the text file. Hashcat will bruteforce the passwords like this:
7a2ecarlos
8j3abigfoot
0t3wguest
6a5jonion
You getting the idea now, right ?
Using so many dictionary at one, using long Masks or Hybrid+Masks takes a long time for the task to complete. It is not possible for everyone every time to keep the system on and not use for personal work and the Hashcat developers understands this problem very well. So, they came up with a brilliant solution which no other password recovery tool offers built-in at this moment. That is the Pause/Resume feature
WPA2 Cracking Pause/resume in Hashcat (One of the best features)
This feature can be used anywhere in Hashcat. It isn't just limited to WPA2 cracking. Even if you are cracking md5, SHA1, OSX, wordpress hashes. As soon as the process is in running state you can pause/resume the process at any moment.
Just press [p] to pause the execution and continue your work.
To resume press [r]. All the commands are just at the end of the output while task execution. See image below
You might sometimes feel this feature as a limitation as you still have to keep the system awake, so that the process doesn't gets cleared away from the memory.
And we have a solution for that too. Create session!
WPA2 Cracking save Sessions and Restore.
Creating and restoring sessions with hashcat is Extremely Easy.
Just add –session at the end of the command you want to run followed by the session name.
Example:
Here I named the session 'blabla'. You can see in the image below that Hashcat has saved the session with the same name i.e blabla and running.
Now you can simply press [q] close cmd, ShutDown System, comeback after a holiday and turn on the system and resume the session. That easy!
NOTE: Once execution is completed session will be deleted.
How to restore ?
Above command – '–restore'. Here it goes:
Hashcat will now check in its working directory for any session previously created and simply resume the Cracking process.
Simple enough ? Yes it is.
This is all for Hashcat. Hope you understand it well and performed it along. No need to be sad if you don't have enough money to purchase those expensive Graphics cards for this purpose you can still try cracking the passwords at high speeds using the clouds. You just have to pay accordingly.
Cloud for Cracking WPA2-PSK
You can even leverage cloud for the same purpose. You just have to pay for the service you use as it requires a lot of money, electricity to keep the system up and running and keeping it fast at the same time.
A Website that provide the similar service is http://cloudcracker.com/ (Discontinued)
They charge $17 for 300 Million words in 20 minutes. Which means 250,000 PMK/Second. Sounds nice! isnt it ?
Crack Wpa2 Fast
Well this is a service so they surely have their part of profit. If you are at a shortage of money you can try even cheaper service.
Don't worry this cheap is actually better than the expensive if you are able to do it accordingly.
That is Amazon Elastic Computing 2(EC2) or AWS (Amazon Web Services). Here you need to do all the things manually after logging into the remote host that yo0u have purchased.
You have to install the tools and dependencies accordingly and give commands to the master server to perform the cracking. You can also create multiple instances to distribute the load and raise the WPA2 cracking speed. Price will change accordingly.
Using Wireshark To Crack Wpa2 With Windows 7
But in short let me tell you if you are willing to do this Super Interesting stuff, it will cost you maximum of $1 an hour for even greater speeds than cloudcracker.
Here is a video to help you understand better the concept of load distribution and command the master server. Hope you are getting the concept.
Here is one more for you to see the WPA2 cracking process running on Amazon EC2, It's an old video but worth watch and understand the concept.
Forgot to tell you one good news. Amazon EC2 is FREE for first year. It will just ask you for the credit/debit card info as a validation proof. But don't worry no extra penny will be deducted until you extend to new plan.
So I would encourage you to do some research on this specific topic after getting over of Hashcat. It is the real Fun believe me!
If you love all this crazy stuff You will love that too.
I discuss all of them in my free WiFi pentesting and Security eBook. Follow the link below to learn more
Download All 10 Chapters of WiFi Pentesting and Security Book…
PDF version contains all of the content and resources found in the web-based guide
Hope this was helpful enough!
Keep Learning.